|
|
登入後,內容更豐富
您需要 登錄 才可以下載或查看,沒有賬號?註冊
×
Vaccine, not Killswitch, Found for Petya (NotPetya) Ransomware Outbreak
- [Bleepingcomputer]
https://www.bleepingcomputer.com ... ansomware-outbreak/
Cybereason security researcher Amit Serper has found a way to prevent the Petya (NotPetya/SortaPetya/Petna) ransomware from infecting computers.
The ransomware has been wreaking havoc across the globe today, locking hard drive MFT and MBR sections and preventing computers from booting. Unless victims opted to pay a ransom (which is now pointless and not recommended), there was no way to recover their systems.
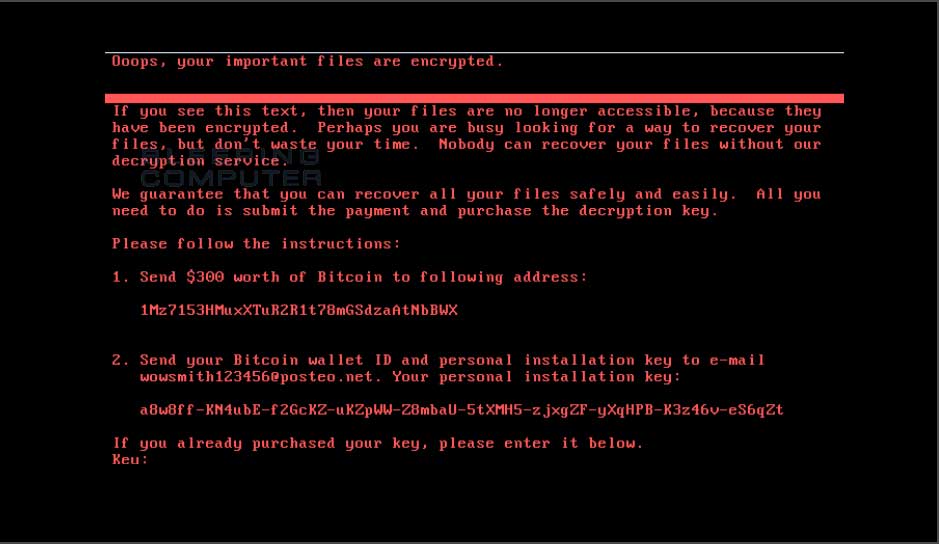
In the first hours of the attack, researchers believed this new ransomware was a new version of an older threat called Petya, but they later discovered that this was a new strain altogether, which borrowed some code from Petya, hence the reason why they recently started it calling it NotPetya, Petna, or as we like to call it SortaPetya.
Researchers flocked to find killswitch mechanism
Because of the ransomware's global outreach, many researchers flocked to analyze it, hoping to find a loophole in its encryption or a killswitch domain that would stop it from spreading, similar to WannaCry.
While analyzing the ransomware's inner workings, Serper was the first to discover that NotPetya would search for a local file and would exit its encryption routine if that file already existed on disk.
The researcher's initial findings have been later confirmed by other security researchers, such as PT Security, TrustedSec, and Emsisoft.
This means victims can create that file on their PCs, set it to read-only, and block the NotPetya ransomware from executing.
While this does prevent the ransomware from running, this method is more of a vaccination than a kill switch. This is because each computer user must independently create this file, compared to a "switch" that the ransomware developer could turn on to globally prevent all ransomware infections.
How to Enable the NotPetya/Petna/Petya Vaccine
To vaccinate your computer so that you are unable to get infected with the current strain of NotPetya/Petya/Petna (yeah, this naming is annoying), simply create a file called perfc in the C:\Windows folder and make it read only. For those who want a quick and easy way to perform this task, Lawrence Abrams has created a batch file that performs this step for you.
Please note that he batch file will also create two addition vaccination files called perfc.dat and perfc.dll. While my tests did not indicate that these additional files are needed, I added them for thoroughness based on the replies to this tweet.
This batch file can be found at: https://download.bleepingcomputer.com/bats/nopetyavac.bat
For those who wish to vaccinate their computer manually, you can do so using the following steps. Please note that these steps are being created to make it as easy as possible for those with little computer experience. For those who have greater experience, you can do it in quite a few, and probably better, ways.
|
|